Press Release
- Deutsche Telekom Network App
- Deutsche Telekom Network Sign In
- Deutsche Telekom Network Speed Test
- Deutsche Telekom Kundencenter
Nokia and Deutsche Telekom Group expand strategic cooperation to build 5G-ready IP network
Deutsche Telekom Global Carrier, the international wholesale unit of Deutsche Telekom, recently turned up the first European 800G network connecting its data centers in Vienna, Austria. Voicestream Wireless free download - Ralink 802.11n Wireless LAN Card, Wireless Key Generator, Realtek RTL8187B Wireless 802.11b/g 54Mbps USB 2.0 Network Adapter, and many more programs. Deutsche Telekom is one of the world's leading integrated telecommunications companies, with some 184 million mobile customers, 27,5 million fixed-network lines, and 21 million broadband lines.
- Deutsche Telekom will deploy the Nokia 7750 Service Router portfolio, designed for the 5G and cloud era, to replace and modernize its existing IP edge/core network in Greece and Hungary initially
- Nokia’s IP edge routers deliver the high-performance, scale and flexibility to support a full array of IP services and functions that meet evolving end user needs
Sim-Card is also installed and device shows in the device manager without problems. But it does not connect to my mobile network. It always says, that there is no reception. When I start the manual search for networks my provider network is shown with LTE. But I cannot choose it. The installed driver is the generic Microsoft Broadband Driver. Wireless data transmission The IoT Service Button transmits alerts via mobile communications and in some regions can already use the new machine network from Telekom based on NarrowBand IoT (NB-IoT). This enables the extremely energy-efficient transmission of small amounts of data from basements and underground production facilities.
12 November 2020
Espoo, Finland – Nokia and Deutsche Telekom Group today announced they are expanding their strategic cooperation to build a 5G-ready IP network. Deutsche Telekom has selected Nokia's 7750 Service Router (SR) platform to significantly expand capacity across its edge/core routing network as it prepares for next-generation broadband and 5G services. Deployment has already started in Greece, where Nokia is replacing and modernizing the operator’s existing IP network. Rollout in Hungary is expected in Q4 2020.
With networks experiencing unprecedented traffic growth and unpredictable demands, operators want to meet ever-increasing performance requirements while driving down network costs. The scale, feature breadth and versatility of the Nokia 7750 SR-s platform addresses these requirements, enabling operators like Deutsche Telekom Group and its affiliates to build bigger, smarter, automated and secure networks with greater return on investment.
As part of its network modernization, Deutsche Telekom needed to replace an existing IP edge/core network that was reaching its end of service with a new network that can cope with 5G and ultra broadband access requirements. A key principle to achieve this was the consolidation of network layers through the integration of IP aggregation and edge/BNG (Broadband Network Gateway) functions into one converged layer.
Deutsche Telekom selected the Nokia 7750 SR-7s routers as they support the full spectrum of provider edge, gateway and core functions for advanced residential, mobile and enterprise services. Powered by the programmable FP4 network processing silicon, the routers will enable Deutsche Telekom to boost IP network capacity with deterministic performace for a top-quality subscriber experience. As a result, Deutsche Telekom can support 5G interconnectivity and an increasing growth in backbone traffic driven by an increase in mobility applications, video streaming, gaming and other high-capacity demands such as remote working.
The 7750 SR-s is managed by the Nokia Network Services Platform (NSP). NSP supports 5G IP transport with automated slicing across IP and optical transport layers with end-to-end orchestration of network resource provisioning and assurance operations. This simplifies operations so that operators can create customer policies/slices with different network performance, quality and routing capabilities to respond quickly to fast-changing subscriber demand.
Bernhard Scholl, Technology Europe VP Access Core & Transport at Deutsche Telekom, said: “Deutsche Telekom Group affiliates need to expand and modernize their IP networks to address stringent 5G IP transport requirements. We continue to see tremendous growth in network traffic and the need to deliver more throughput and higher capacity with strict QoS to our customers is critical. This is particlarly the case as bandwidth intensive applications are shifting to on demand video along with the growing usage of cloud-based services. Building out this backbone with Nokia's IP edge routers will allow us to stay ahead of our customers’ network needs.”
Vassilis Kazatzopoulos, Head of International Sales DT Global Customer Business Team at Nokia, said: “With trends like 5G, IoT and Industry 4.0 now a reality, networks are expected to handle hundreds of new applications and services for millions of users. The Nokia 7750 SR-s series of IP routers takes router performance to the next level by delivering the massive scale, comprehensive feature set and platform versatility needed to stay ahead of evolving demands. Nokia is excited to expand its longstanding relationship with Deutsche Telekom Group to help prepare its affiliates’ networks for the future.”
Resources:
- Webpage:Nokia 7750 Service Router (SR)
- Webpage:Nokia FP4 network processor
- Webpage:Network Services Platform (NSP)
About Nokia
We create the technology to connect the world. Only Nokia offers a comprehensive portfolio of network equipment, software, services and licensing opportunities across the globe. With our commitment to innovation, driven by the award-winning Nokia Bell Labs, we are a leader in the development and deployment of 5G networks.
Our communications service provider customers support more than 6.4 billion subscriptions with our radio networks, and our enterprise customers have deployed over 1,300 industrial networks worldwide. Adhering to the highest ethical standards, we transform how people live, work and communicate. For our latest updates, please visit us online www.nokia.com and follow us on Twitter @nokia.
Media Inquiries:
Nokia
Communications
Phone: +358 10 448 4900
Email: press.services@nokia.com
Download dibcom usb devices driver updater.
More articles issued by Nokia Oyj
More articles related to:
Press releases
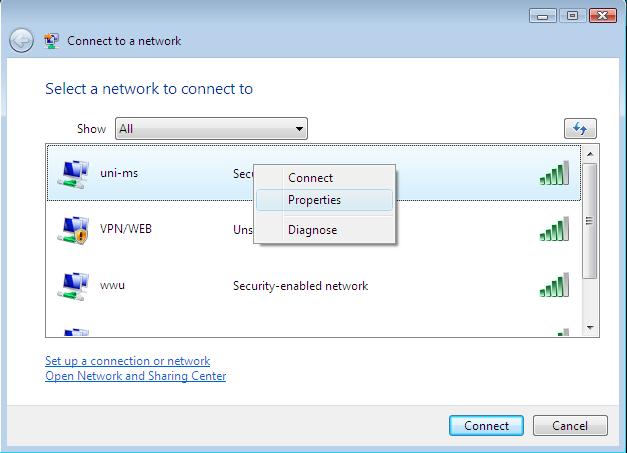
We created a honeypot platform, which is based on the well-established honeypots glastopf, kippo, honeytrap and dionaea, the network IDS/IPS suricata, elasticsearch-logstash-kibana, ewsposter and somedocker magic. We want to make this technology available to everyone who is interested and release it as a Community Edition. We want to encourage you to participate.
- Meet the system requirements. Use at least 2GB RAM and 40GB disk space as well as a working internet connection.
- Download the tpotce.iso or create it yourself.
- Install the system in a VM or on physical hardware with internet access.
- Sit tight - watch and analyze.
We have created a nice installation video for you in case you run into problems. Pleasebe advised, that one CPU is fully sufficient to run T-Pot.
Update: In case you already have an Ubuntu 14.04.x running in your datacenter and are unable to install from an ISO image, we have created a script that converts your Ubuntu base install into a full-fledged T-Pot within just a couple of minutes.
Please note: We will ensure the compatibility to the Intel NUC platform, as we really like this handy format.
- Installation
- Options
In the last couple of years, we at Deutsche Telekom’s honeypot project have setup several honeypots in our home networks, Telekom’s access networks and at partner locations all around the globe. The data gathered by those honeypots is a core component for our Early Warning System and feeds the data for the Sicherheitstacho / “Securitydashboard”.
Our experience in setting up honeypot systems at several locations showed that many people were interested in running some kind of honeypot sensor, but were a bit overwhelmed by the setup procedure and maintenance. In the past, we have gathered some experience with configuration management and finally decided to create a honeypot system that is easy to deploy, low maintenance and combines some of the best honeypot technologies in one system.
Lucky for us, a new technology called docker emerged and we thought we’d give it a try…
Fast forward a couple of months: We finally created a multi-honeypot platform, that we want to make available as a public beta in order to foster a community and make this technology available to all people interested.Aside from this, we also want to motivate people to contribute to security research and maybe take a first step towards cooperation and data exchange.
Our solution is no silver bullet to security, no intrusion prevention system and it’s no fancy, cutting edge APT detection tool…
But let’s focus on what it is: Some of the best honeypot technologies available, easy to deploy and simple use.
T-Pot is based on well-established honeypot daemons, IDS and tools for attack submission.
The idea behind T-Pot is to create a system, whose entire TCP network range as well as some important UDP services act as honeypot, and to forward all incoming attack traffic to the best suited honeypot daemons in order to respond and process it.
T-Pot is based on a vanilla Ubuntu 14.04.02 ISO image. The honeypot daemons as well as other support components we used have been paravirtualized using docker.This allowed us to run multiple honeypot daemons on the same network interface without problems make the entire system very low maintenance.
The encapsulation of the honeypot daemons in docker provides a good isolation of the runtime environments and easy update mechanisms.
In T-Pot we combine existing honeypots (glastopf, kippo, honeytrap and dionaea) with the network IDS/IPS suricata, the data monitoring and visualization triple elasticsearch-logstash-kibana, and our own data submission ewsposter which now also supports hpfeeds honeypot data sharing.
All data in docker is volatile. Once a docker container crashes, all data produced within its environment is gone and a fresh instance is restarted. Hence, for some data that needs to be persistent, like config files etc., we have a persistent data storage (mounted to /data/ on the host) in order to make it available and persistent across container or system restarts.
Basically, what happens when the system is booted up is the following:
- start host system
- start all docker containers (honeypots, IDS, elk, ewsposter)
- ewsposter periodically checks the honeypot containers for new attacks and submits data to our community backend
Within the T-Pot project, we provide all the tools and documentation necessary to build your own honeypot system and contribute to our community data view, a separate channel on our Sicherheitstacho that is powered by this community data.
The source code and configuration files are stored in individual github repositories, which are linked below. The docker images are tailored to be run in this environment. If you want to run the docker images separately, make sure you study the upstart scripts, as they provide an insight in how we configured them.
The individual docker configurations etc. we used can be found here:
Whether you install it on real hardware or in a virtual machine, make sure your designated T-Pot system meets the following minimum system requirements:
- 2 GB RAM (4 GB recommended)
- 40 GB disk (64 GB SSD recommended)
- Working internet connection / network via DHCP
The installation of T-Pot is simple. Please be advised that you should have an internet connection up and runningas even the installation iso file will need the basic docker containers to be pulled from docker hub.
First, decide if you want to download our prebuilt installation ISO image tpotce.isoorcreate it yourself.
Second, decide where you want to let the system run: real hardware or in a virtual machine?
Prebuilt ISO Image
We provide an installation ISO image for download (~610MB), which is created using the same tool you can use yourself in order to create your own image. It will basically just save you some time downloading components and creating the ISO image. You can download the prebuilt installation image here and jump to the installation section. The ISO image is hosted by our friends from Strato / Cronon.
Create your own ISO Image
For transparency reasons and to give you the ability to customize your install, we provide you the tool that enables you to create your own ISO installation image.
Requirements to create the ISO image:
- Ubuntu 14.04.2 or 14.10 as host system (others may work, but remain untested)
- 2GB of free memory
- 4GB of free storage
- A working internet connection
How to create the ISO image:
Clone the repository and enter it.
Invoke the script that builds the ISO image. The script will download and install dependencies necessary to build the image on the invoking machine. It will further download the Ubuntu base image (~625MB) which T-Pot is based on.
Running in VM
You may want to run T-Pot in a virtualized environment. The virtual system configuration depends on your virtualization provider.
We successfully tested T-Pot with VirtualBox and VMWare with just little modifications to the default machine configurations.
It is important to make sure you meet the system requirements and assign a virtual harddisk >=40GB, >=2GB RAM and bridged networking to T-Pot.
You need to enable promiscuous mode for the network interface for suricata to work properly. Make sure you enable it during configuration.
If you want to use a wifi card as primary NIC for T-Pot (which we do not recommend, but in some cases, it might be necessary), mind that not all network interface drivers support all wireless cards. E.g. in VirtualBox, you then have to choose the “MT SERVER” model of the NIC.
Last, mount the tpotce.iso ISO to the VM and and continue with the installation. You can now jump here.
Running on Hardware
If you decided to run T-Pot on dedicated hardware, just follow these steps:
- Burn a CD from the ISO image or make a bootable USB stick using the image.
Whereas most CD burning tools allow you to burn from ISO images, the procedure to create a bootable USB stick from an ISO image depends on your system. There are various Windows GUI tools available, e.g. this tip might help you.
On Linux or MacOS you can use the tool dd or google for GUI tools. - Boot from the USB stick and install.
First Run
The installation requires very little interaction, only some locales and keyboard settings have to be answered. Most other things should be configured automatically. The system will reboot a couple of times. Make sure it can access the internet as it needs to download the dockerized honeypot components. Depending on your network connection, the installation may take some time. During our tests, the installation was finished within 30 minutes.
Once the installation is finished, the system will automatically reboot and you will be presented with the T-Pot login screen. The user credentials for the first login are:
- user: tsec
- pass: tsec
Deutsche Telekom Network App
You will need to set a new password after first login.
All honeypot services are started automatically.
Make sure your system is reachable through the internet. Otherwise it will not capture any attacks, other than the ones from your hostile internal network! Drivers dku-5 connectivity adapter cable free. We recommend you put it in an unfiltered zone, where all TCP and UDP traffic is forwarded to T-Pot’s network interface.
If you are behind a NAT gateway (e.g. home router), here is a list of ports that should be forwarded to T-Pot.
| Resonding Honeypot | Transport | Port(s) to forward |
|---|---|---|
| dionaea | TCP | 21, 42, 135, 443, 445, 1433, 3306, 5060, 5061, 8080 |
| dionaea | UDP | 69, 5060 |
| kippo | TCP | 22 |
| honeytrap | TCP | 25, 110, 139, 3389, 4444, 4899, 5900, 21000 |
| glastopf | TCP | 80 |
Basically, you can forward as many TCP ports as you want, as honeytrap dynamically binds any TCP port that is not covered by the other honeypot daemons.
In case you want external SSH access, forward TCP port 64295 to T-Pot, see below.
T-Pot requires outgoing http and https connections for updates (ubuntu, docker) and attack submission (ewsposter, hpfeeds).
The system is designed to run without any interaction or maintenance and contribute to the community.As we know, for some this may not be enough. So here come some ways to further inspect the system and change configuration parameters.
Enabling SSH
By default, the ssh daemon is disabled. However, if you want to be able to login via SSH, make sure you enable it like this:
This will start the SSH daemon on port 64295. It is configured to prevent password login and use pubkey-authentication instead, so make sure you get your key on the system. Just copy it to /home/tsec/.ssh/authorized_keys and set the appropriate permissions (chmod 600 authorized_keys) as well as the right ownership (chown tsec:tsec authorized_keys).
In addition to this - and maybe easier than getting a pubkey on the system - you can enable two-factor authentication (2fa) and use an app like Google Authenticator as a second authentication factor.
Make sure that you invoke the following script as the user tsec. Do not run it as root or via sudo. Otherwise the setup of two factor authentication will fail.
Don’t forget to enable ssh, if you haven’t done this before. If you already have enabled ssh, restart the ssh daemon sudo service ssh restart to make sure that the changes are active.
You can then login using the password you set for the user tsec and use the app as the second authentication factor.
Kibana Dashboard
To access the kibana dashboard, make sure you have enabled SSH on T-Pot, then create a port forward and make sure you leave the terminal open.
Finally, open a web browser and access http://127.0.0.1:8080. The kibana dashboard can be customized to fit your needs. By default, we haven’t added any filtering other than outgoing ewsposter submission, because the filters depend on your setup. E.g. you might want to filter out your incoming administrative ssh connections and connections to update servers.
Maintenance
As mentioned before, the system was designed to be low maintenance. Basically, there is nothing you have to do but let it run. If one of the dockerized daemon fails, it will restart. If this fails, all docker container will be restarted.
If you run into any problems, a reboot may fix it. ;)
If new versions of the components involved appear, we will test them and build new docker images. Those new docker images will be pushed to the system and get restarted.
Community Data Submission
We provide T-Pot in order to make it accessible to all people who are interested in honeypot deployment. By default, the data captured is submitted to a community backend. This community backend uses the data to feed a community data view, a separate channel on our own Sicherheitstacho, which is powered by our own set of honeypots.You may opt out the submission to our community server by disabling it in the [EWS]-section of the config file /data/ews/conf/ews.cfg.
Further we support hpfeeds. It is disabled by default as you need to supply a channel you want to post to and enter your user credentials. To enable hpfeeds, edit the config file /data/ews/conf/ews.cfg, section [HPFEED] and set it to true.
Download gateway monitors driver. Gateway Monitor Drivers free download - CopyTrans Drivers Installer, Adaptec ASPI Drivers, Microsoft DirectX Drivers (Windows 95), and many more programs. Download Gateway monitor drivers or install DriverPack Solution software for driver scan and update. Download Download DriverPack Online. All Gateway monitors. FHD2303L (Analog) FHD2303L (Digital) FHD2303L (HDMI) FPD1520. Drivers & Downloads. Locate drivers, user guides and product specifications for your Gateway technology. Get smart comprehensive solutions to your technology questions about your particular product. Download drivers for monitor for Gateway M-2409J laptop for Windows 7, XP, 10, 8, and 8.1, or download DriverPack Solution software for driver update. Popular Drivers. Gateway C-140X monitors Fujitsu LifeBook U1010 monitors Fujitsu LifeBook S7111 monitors Fujitsu LIFEBOOK T726 monitors.
Data is submitted in structured ews-format, a XML stucture. Hence, you can parse out the information that is relevant to you.
We encourage you not to disable the data submission as the main purpose of the community is sharing.
Deutsche Telekom Network Sign In
The ews.cfg file contains many configuration parameters required for the system to run. You can - if you want - add an email address, that is sent within your submissions, in order to be able to identify your requests later. Further you can add a proxy.Please do not change anything other than those settings and only if you absolutely need to. Otherwise, the system may not work as expected.
We planned a couple of features we haven’t been able to implement yet. Those features will most likely be added through automatic updates of the docker containers.
- Import ews json log into kibana dashboard in order to visualize captured attack data
- Filter out false positives in kibana dashboard (e.g. update connections)
- We don’t have access to your system. So we cannot remote-assist when you break your configuration. But you can simply reinstall.
- The software was designed with best effort security, not to be in stealth mode. Because then, we probably would not be able to provide those kind of honeypot services.
- You install and you run within your responsibility. Choose your deployment wisely as a system compromise can never be ruled out.
- Honeypots should - by design - not host any sensitive data. Make sure you don’t add any.
- By default, your data is submitted to the community dashboard. You can disable this in the config. But hey, wouldn’t it be better to contribute to the community?
- By default, hpfeeds submission is disabled. You can enable it in the config section for hpfeeds. This is due to the nature of hpfeeds. We do not want to spam any channel, so you can choose where to post your data and who to share it with.
- Malware submission is enabled by default but malware is currently not processed on the submission backend. This may be added later, but can also be disabled in the ews.cfg config file.
- The system restarts the docker containers every night to avoid clutter and reduce disk consumption. All data in the container is then reset. The data displayed in kibana is kept for the last 30 days.
- This software is in beta status, so it may contain bugs.
- Q : How do I enable SSH?
A : Run the ssh_enable.sh script in tsec’s home directory. More here. - Q : On what port is the SSH daemon listening?
A: OpenSSH is listening on port 64295. More here. - Q : Why didn’t you add honeypot XYZ?
A : We added the honeypot daemons which we thought were most suitable and we have good experience with. If you think a crucial honeypot daemon is missing, let us know. Maybe someday we will add it. - Q : Why is my installation failing?
A : Some people have tried to install it in VirtualBox using the default disk size of 8GB. This is not enough storage and the installation will fail. Same applies to VMWare’s Easy Install. Make sure you meet the system requirements. T-Pot requires at least 2GB RAM and 40GB disk space. And make sure that a working internet connection is available. - Q : I try to login via ssh but my ssh key gets rejected?
A: Are you sure you are connecting to the right port? The SSH honeypot kippo is listening on port 22. OpenSSH is listening on port 64295. More here. Q : I enabled two-factor authentication, but all I get is a password prompt and it does not accept my password. What happened?
A : You probably invoked the2fa_enable.shscript (a) as root or (b) via sudo, and you should have invoked it as the user tsec.
Fix for (a):- Q : I cannot expose T-Pot to full internet access, but I still want to participate. Can you tell me which ports should be forwarded to T-Pot?
A : T-Pot works best when exposed to the unfiltered internet. If you are unable to place it in that way, here is a list of ports that should be forwarded to T-Pot.
… to be extended depending on feedback.
We provide the software as it is as a Community Edition. T-Pot is designed to run out of the box and with no maintenance effort.
We hope you understand that we are unable to provide support on an individual basis. We will try to answer common questions and problems in the Q&A section.
Deutsche Telekom Network Speed Test
Please understand that we cannot provide support on an individual basis. We will try to address questions, bugs and problems on our GitHub issue list.
Deutsche Telekom Kundencenter
The software that T-Pot is built on, uses the following licenses.
GPLv2: dionaea, honeytrap (by Tillmann Werner), suricata
GPLv3: ewsposter (by Markus Schroer), glastopf (by Lukas Rist)
Apache 2 License: elasticsearch, logstash, kibana, [docker] (https://github.com/docker/docker/blob/master/LICENSE)
kippo copyright disclaimer (by Upi Tamminen)
Ubuntu licensing